Since cybersecurity has become more important, VPNs are becoming more and more essential in our lives. Amid increasingly diverse user needs and the gradual refinement of network technology, many types of VPN tunnels have evolved to be used in a variety of different scenarios.
This article will introduce you to several commonly used VPNs and various VPN protocols, helping you gain a better understanding of VPN products.
Main Types of VPN
Here are the main VPN types people are using today.
Site-to-Site VPN – Mainly Used by Business
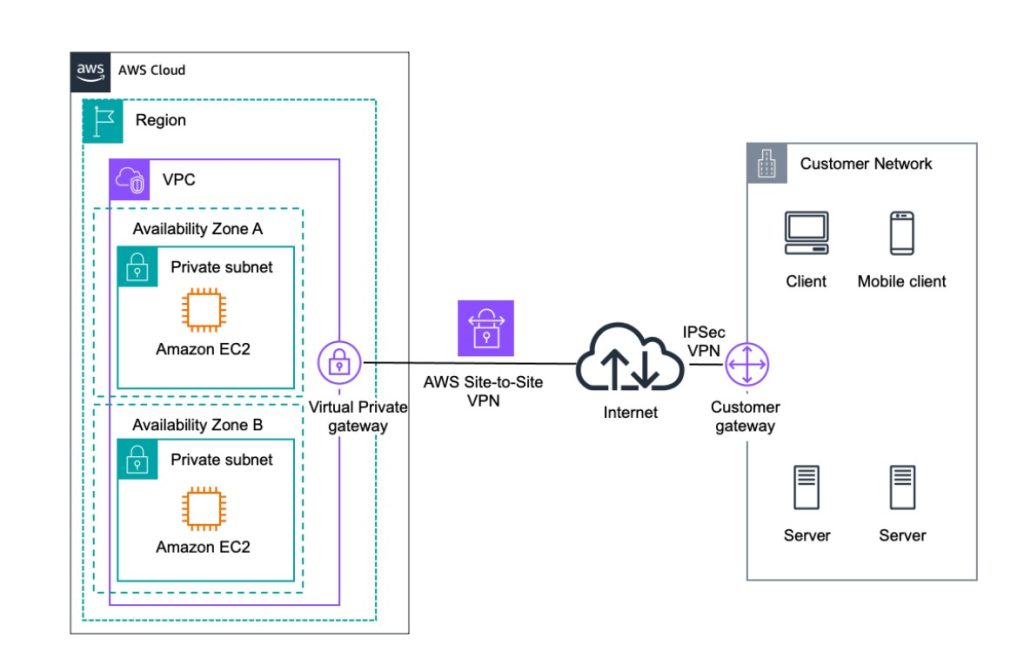
Site-to-site VPN is one of the VPN types widely used today. It is normally used by large institutions like offices. Two collaborating companies or a parent company and its subsidiary can set up this type of VPN to achieve resource sharing.
The working principle is easy to understand. With the VPN protocols, a site-to-site VPN can create an encryption tunnel and reroute one company’s internet traffic to another corporation, making them seem together. Then, the VPN gateway of the destination will give authentication to this redirected traffic and let it in, so the sender can access the destination’s network and resources.
Site-to-site VPNs typically handle large volumes of traffic, so they require very high performance and security to ensure the safe and fast transmission of important corporate documents and resources.
Currently, cloud-based site-to-site VPNs available on the market include AWS, Microsoft Azure, Google Cloud Platform, and others.
Remote Access VPN – Employee’s Top Option
Remote Access VPN is also one of the types of VPN. It is mainly used by an employee to gain the company’s files and data. This VPN redirects the user’s online traffic to his company, and then after getting permission, he can enter the protected database.
Remote Access VPN processes relatively less traffic so it doesn’t need to meet the requirement of high speed and performance. Remote access VPN is very flexible to use, allowing employees to adopt it while traveling for business or working from home.
Remote access VPNs are primarily suitable for individuals accessing repositories at other locations, so the setup cost is relatively low. Nowadays, common enterprise remote access VPNs on the market include Palo Alto GlobalProtect, Cisco AnyConnect, and NordLayer, among others.

Personal or Business VPN – Tool for Entertainment
This VPN type is generally used by an average person to stream or play online games from geo-limited countries or regions. Compared to the former two VPNs, this VPN comes from a VPN provider and can help access a larger map of the world. It is usually downloaded as software or an application on various personal devices. It requires a usable Wi-Fi network.
For example, LightningX VPN is one of the best personal VPNs today, allowing users to change IP addresses to 2,000+ specific regions around 50+ countries. It is also one of the types of VPN for Android. Unlike site-to-site VPNs or remote access VPNs, LightningX VPN can be directly installed on computers, phones, tablets, and TVs.
However, personal VPNs can still be used as remote access VPNs but not for business use. A VPN for remote access requires the authentication of the company to join the network while personal VPNs can only help surf the public internet web.
Cloud VPN – Cloud-Based and Easy to Manage
Cloud VPN is a virtual private network based on the cloud. Very different from the former three VPNs, a cloud VPN is quicker to access content online and covers vast of the world.
It works by routing users’ internet traffic through an encryption tunnel to the cloud service provider. Then, the provider will send users’ requests to the websites and return the answers to users in the same way.
A company doesn’t need to manage and repair the VPN devices because they are owned by the cloud service provider. This could save a lot of time and effort for the company.
The cloud VPN examples in the market include Perimeter 81, VyprVPN for Business, and Surfshark.
Types of VPN Protocols – Ranked
WireGuard – Best VPN Protocol
WireGuard is widely recognized as a top-tier VPN protocol for its lightweight nature and exceptional performance. As an open-source protocol, WireGuard offers advantages such as transparency, timely fixes, customizability, and free, making it a top choice in terms of technology and user support.
WireGuard’s lightweight nature allows it to be compatible with nearly all platforms and makes it easy for users to review. It employs key routing technology to assign static IP addresses to users and manage their traffic, which significantly reduces latency and simplifies the setup process, thereby enhancing performance.
IKEv2/IPsec – Top Choice for Mobile Users
Internet key exchange version 2 (IKEv2) is often used in conjunction with Internet Protocol Security (IPSec). IKEv2 creates a tunnel between the user and the VPN server while IPSec encrypts and authorizes it.
The two protocols are designed for mobile usage. Users can frequently switch networks using them. Meanwhile, the switch won’t affect the fast speed and the stability of IKEv2. However, unlike WireGuard’s full compatibility, IKEv2 is limitedly compatible with Windows devices.
OpenVPN – Business-Preferred VPN Protocol
OpenVPN is frequently used by different types of VPNs. It is open-source and highly secure, commonly used in point-to-point and site-to-site VPN configurations utilized by enterprises. OpenVPN encapsulates data through SSL/TLS encryption, safeguarding enterprise data security.
However, OpenVPN may not be suitable for non-technical users, as it involves technologies that can be quite complex.
SSTP – Robust Traversing Ability
The Secure Socket Tunneling Protocol (SSTP) is a VPN communication protocol that uses SSL/TLS encryption to ensure the security of data during transmission over the Internet.
Additionally, because SSTP uses the standard HTTPS port, it can easily bypass most firewalls and network restrictions. However, since it is a protocol designed for Windows users, it lacks compatibility with other platforms.
L2TP/IPsec – VPN Tunneling Protocol
L2TP is a tunneling protocol that doesn’t provide encryption while IPSec can help it make up for the limitation, so they are commonly paired to use. L2TP encapsulates data packets and transmits them through the Internet while IPSec encrypts the transmission.
L2TP/IPSec is often adopted by businesses because it is simple to set up and supports multiple platforms and devices. However, L2TP is somewhat inferior in terms of speed and its ability to bypass heavily encrypted firewalls.
PPTP – One of the Oldest Types of VPN Protocols
Point-to-Point Tunneling Protocol (PPTP) is an old VPN protocol designed by Microsoft. This protocol is easy to set up and offers fast connection speeds, but it has weak security, making it suitable for users who prioritize streaming videos or gaming speed over security.
PPTP is often used on older devices due to its compatibility. However, because of its weak security, it is generally not adopted by enterprises.
Conclusion
The VPN types we have listed for you are actually based on today’s user needs and implementation methods. In fact, VPNs can also be categorized according to other classification ways. You can even customize your own VPN based on usage scenarios, requirements, and budget.
















