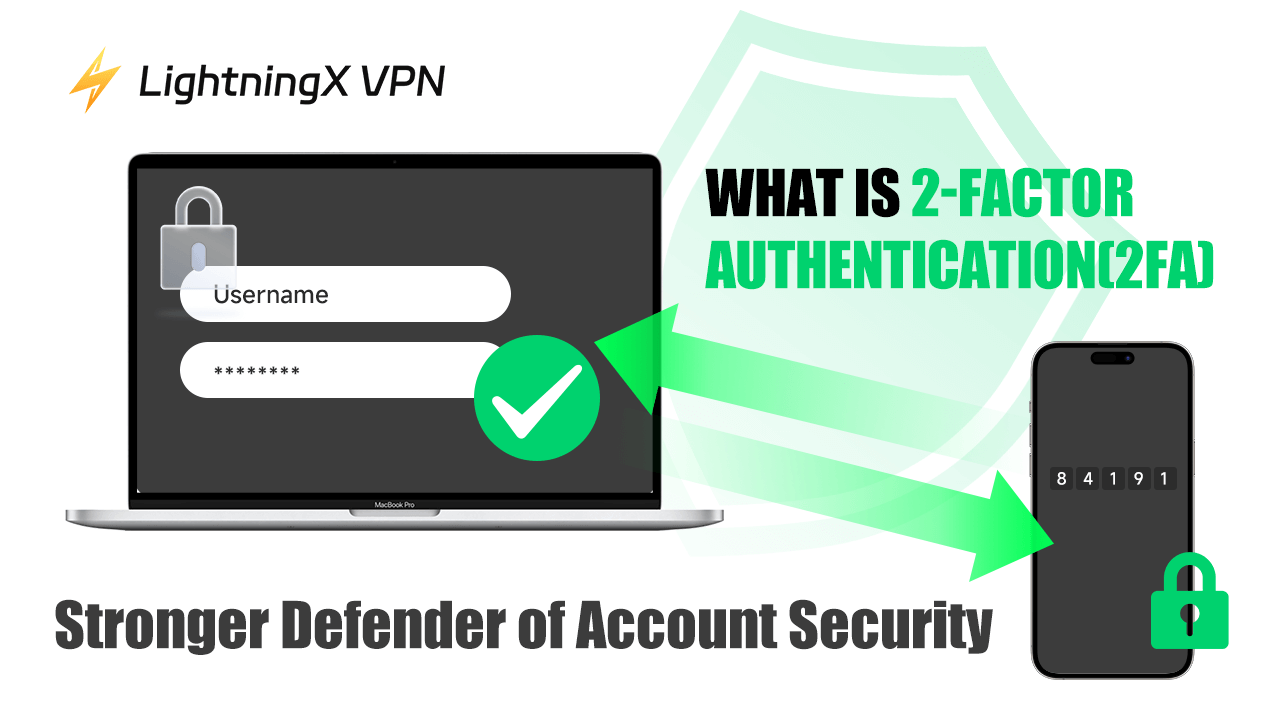
What is 2-factor authentication?We hear about data breaches, hacked accounts, and stolen identities almost every day. Most of us use passwords to protect our online accounts, but passwords alone are not always enough. This is where 2-Factor Authentication (2FA) comes in.
2FA adds an extra layer of security to your accounts, making it harder for hackers to gain access. This blog will explain what 2-factor authentication is, its importance and its types, how it works, and how to set up it.
What is 2-Factor Authentication?
2-Factor Authentication, or 2FA, is a security process that requires two forms of identification before you can access an account. Think of it as a double lock on your door. Even if someone has one key, they need another to get inside.
The same idea applies to 2FA. When you log in to an account, you need your password (something you know) and a second factor (something you have).
The second factor can be a text message code, an app notification, a fingerprint, or even facial recognition. This makes it much harder for hackers to break in, even if they have your password.
Why Should You Care About 2FA?
Why should I care about 2-factor authentication? This part will give you the answers.
1. The Limitations of Passwords Alone
- Passwords are often the weakest link in security.
- Easy to guess (birthdays, pet names, etc.).
- Commonly reused across multiple accounts.
- Vulnerable to harmful attacks.
- 81% of data breaches are caused by weak or stolen passwords (see Verizon Data Breach Investigations Report).
- Even complex passwords can be compromised through phishing or keylogging.
2. Rising Cybercrime Statistics
- Cybercrime damages are expected to reach $10.5 trillion annually by 2025 (Cybersecurity Magazine).
- 300 billion passwords in used globally by 2020 (Cybersecurity Magazine).
- 30,000 websites are hacked every day (Forbes).
- 80% of data breaches could be prevented with basic actions, including 2FA (Cited from the US national cyber security chief).
3. Individual Case Study of a Security Breach
The 2014 iCloud celebrity photo leak (Forbes):
- Hackers gained access to celebrities’ iCloud accounts.
- Used phishing and password guessing to breach accounts.
- Resulted in private photos being leaked online.
- Apple responded by encouraging the use of 2FA.
- Warning: Even high-profile individuals can fall victim to simple hacking techniques.
Pros and Cons of 2FA
The Pros of 2FA
1. Improvement of Account Security
- Adds an extra layer of protection beyond passwords.
- Reduces the risk of unauthorized access by up to 99% (Google).
- Makes it exceedingly harder for attackers to gain access, even if they have your password.
- Protects against online attacks where hackers use stolen username/password combinations.
Tips:
Other than 2FA’s strong security, VPN also enhances your online safety. Here we recommend one of the best VPN services: LightningX VPN. With it, your data is protected by advanced encryption like Shadowsocks and Vless. This ensures that your sensitive information is safe from hackers.
2. Protection Against Common Hacking Techniques
- Phishing: Even if you accidentally give away your password, the attacker still can’t access your account without the second factor.
- Keylogging: Captures your password but not your second factor.
- Brute force attacks: Rendered ineffective as the password alone is not sufficient.
- MITM (Man in the middle) attacks: The second factor often uses a separate channel, making interception more difficult
The Cons of 2FA
Potential Inconvenience:
- Extra steps are required for each login.
- Can be terrible if you don’t have immediate access to your second factor (e.g., leaving your phone at home).
- May require multiple 2FA setups for different accounts.
- Some users find it tedious and may attempt to disable it.
How Does 2-Factor Authentication Work?
2FA works by combining two types of identification.
Step 1. Enter Your Password
First, you enter your username and password like you usually do. This is the first factor of authentication, which is something you know.
Step 2. Verify with a Second Factor
After entering your password, you need to verify your identity with a second factor. Types of the second factor will be introduced later.
Step 3. Access Granted
Once you successfully enter both factors, you are granted access to your account. This process may seem like it takes more time, but it adds a critical layer of protection.
Types of 2-Factor Authentication Methods
There are several types of 2FA.
1. SMS-Based 2FA
This method sends a one-time code to your mobile phone via text message. It is easy to use but can be vulnerable to SIM-swapping attacks. In this case, hackers trick the mobile carrier into transferring the victim’s phone number to their SIM card.
2. Authenticator Apps
Authenticator apps like Google Authenticator or Microsoft Authenticator generate codes that refresh every 30 seconds. These are more secure than SMS because they are not dependent on your phone number.
3. Hardware Tokens
Physical devices like YubiKey are used to generate codes or provide direct access. These are highly secure but can be inconvenient if you lose the device.
4. Biometric Authentication
This uses your physical features, like fingerprints or facial recognition, and even voice recognition, to confirm your identity. It’s very secure but requires devices that support biometric scanning.
5. Email-based 2FA
Some platforms use email to send a one-time code. It’s convenient but not as secure because emails can be intercepted.
Related: 15 Internet Safety Tips: Everyone Should Know
How to Set Up 2-Factor Authentication
Setting up 2FA is simple and varies slightly depending on the platform. Here’s a general guide:
1. Go to Account Settings
Find the security settings in your account. Look for options like “Security,” “Login,” or “2-Factor Authentication.”
2. Choose a 2FA Method
Decide which 2FA method you prefer. You can choose between SMS codes, an authenticator app, or Biometric recognition.
3. Follow the Instructions
Follow the on-screen instructions to set up 2FA. You may need to provide your phone number or download an authenticator app.
4. Save Backup Codes
Many services offer backup codes in case you lose access to your phone or second factor. Save these codes in a safe place.
5. Test the Setup
After setting up 2FA, log out and try logging back in to ensure everything works correctly.
FAQs – What is 2-Factor Authentication?
1. What If I Lose My Phone?
Losing your phone can be stressful, but most services provide backup codes or alternative methods to access your account. Make sure to keep these backup codes in a safe place.
2. Is 2FA Inconvenient?
Some people find 2FA a bit inconvenient because it adds an extra step. However, the added security far outweighs the minor inconvenience.
3. Can 2FA Be Hacked?
While no system is 100% secure, 2FA significantly reduces the risk of hacking. It is much harder for a hacker to gain access when two factors are required.
Conclusion
What is 2-factor Authentication? 2-Factor Authentication provides an extra layer of security, protecting your personal information and online accounts from hackers. This blog covers what 2-factor Authentication is, why it matters, how it works, its different types, and how to set it up. Check your 2FA for stronger online safety!